Live TV feature added to Media Home System
I’ve posted about creating a media home system using Kodi sometimes ago.
After that I configured Kodi on my Laptop and Smart phone which they use the same database shared in home network.
Now, with the help of a small TV card, I’ve added live TV feature to the whole media home.
How to Turn an Old PC Into NAS
Recently, I collected my old Hard drives (and CD/DVD writers) and packed them into my OLD Computer Case in order to create home NAS . Then I’ve installed FreeNAS on it and everything is OK. 🙂
FreeNAS is the simplest way to create a centralized and easily accessible place for your data
Following, the construction steps are presented.
Miner Found!
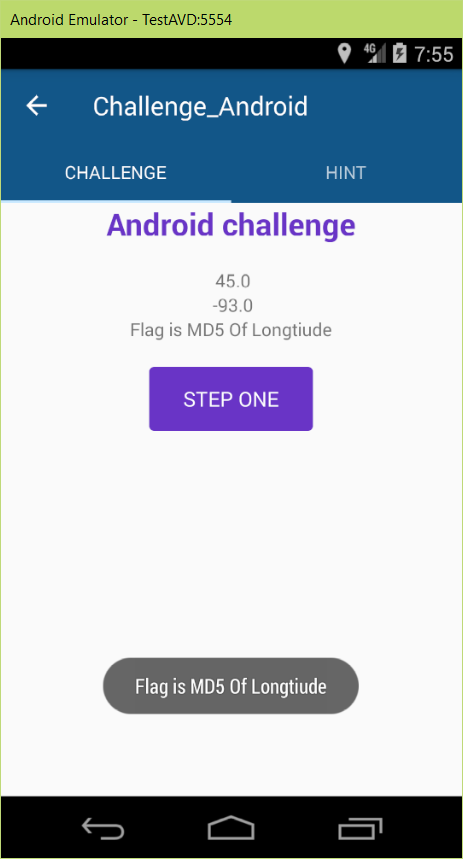
8st SharifCTF Android WriteUps: Vol I
Barnamak WriteUp
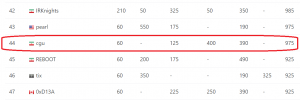
Two weeks ago, SharifCTF was hold and the questions were acceptable. We attended with CGU team name and and gain the 44th place among the 682 attended teams, whom has at least one question solved in the CTF. In this post I described the writeup for the question about reverse engineering of Android app with 200 points (the 3rd question of reverse section).
Your Radio: Broadcast Yourself!
As I told in About Mir Saman section, I love classical musics. I used to listen to online classical radios which are broadcasting the musics 24×7. I was wondering how these services are working. In this post I will show you how to create an online radio broadcast station from your computer.
“Introduction to Cryptography and PGP” Workshop
I have a workshop titled “Introduction to Cryptography and PGP” at Urmia University of Technology. I talked about basic concepts of signature and encryption using asymmetric cryptography. Then I talked about PGP which is one of the main usages of this system. I followed the workshop with configuring Thunderbird and GPG4win for applying PGP in Email system. You may find the contents in my previous post about GPG in Thunderbird and the way PGP works.
The pictures of this session is here.
PGP: How it works?
In “Encrypting Emails using PGP/GPG”, I have described how to configure GPG (PGP) + Enigmail + Thunderbird for sending signed and encrypted emails. But the inner process of PGP is not described. In this post, I will describe how PGP works and the emulation process of PGP will be covered by the nice cryptography tool named cryptoolv2.