Last Wednesday, I have a small talk about SQLi web application vulnerability and how to prevent it. Here, I write about the tools and resources which can be used in learning the SQLi learning and prevention.

The one of the best resources for learning lies in practicing. Practice make perfect. Therefore, penetration the vulnerable web application will make the learning much easier. Damn Vulnerable Web Application (DVWA) is one the vulnerable web applications for learning why and how the applications gets the vulnerabilities.
Some of sample injections tests on the special VM I’ve created for this session is below:


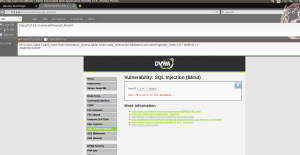
The other tools are for dynamically analyzing web application:
I also talked about how to statically analyze the web application. I’ve introduced RIPS which is the one of the most powerful frameworks for finding bugs in web application. The following image is a screenshot of RIPS scanner for DVWA 1.9.
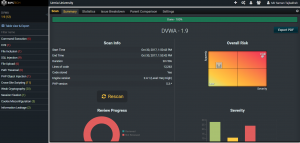
Also the Web Application Firewalls (WAFs) will help web servers before passing the user input to the vulnerable web application such as ModSecurity which can be handle user input along with Apache, and other WAFs …
In the end the session ended with some fun. 🙂
You may follow the sessions from UUT CEIT group:
or in their web site at UUTidev



