Onion Tunnel: Proxy Every TOR Hidden Service on localhost
Onion Tunnel
Onion Tunnel is a simple tunnel app for tunneling every connection through TOR network. It is in my GitHub repository named OnionTunnel: https://github.com/mirsamantajbakhsh/OnionTunnel.
TOR Android Library
In previous post, I’ve talked about compiling TOR from source in Android and added some helper libraries for starting and configuring TOR. In this post, I’ve created a library based on Tor Binary (version 0.4.4.0) and published in GitHub, JFrog and JitPack.
Onion Balance v2: Beautiful Load Balancer in TOR
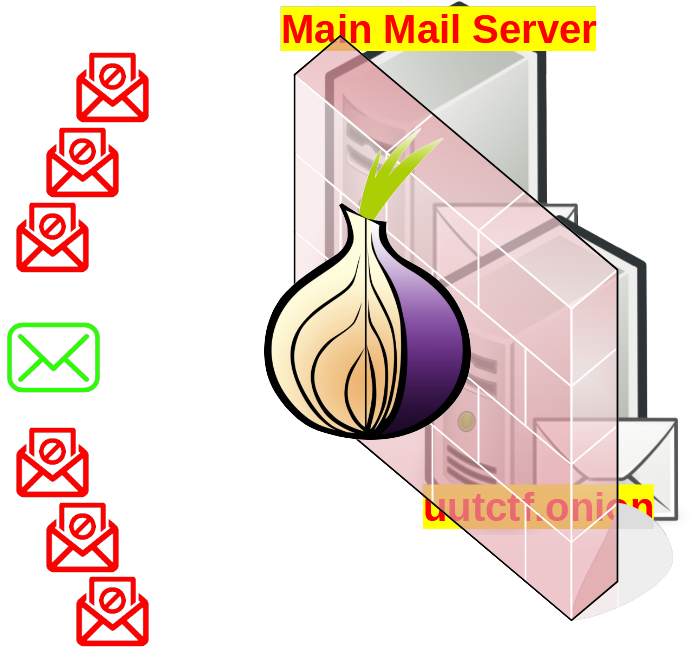
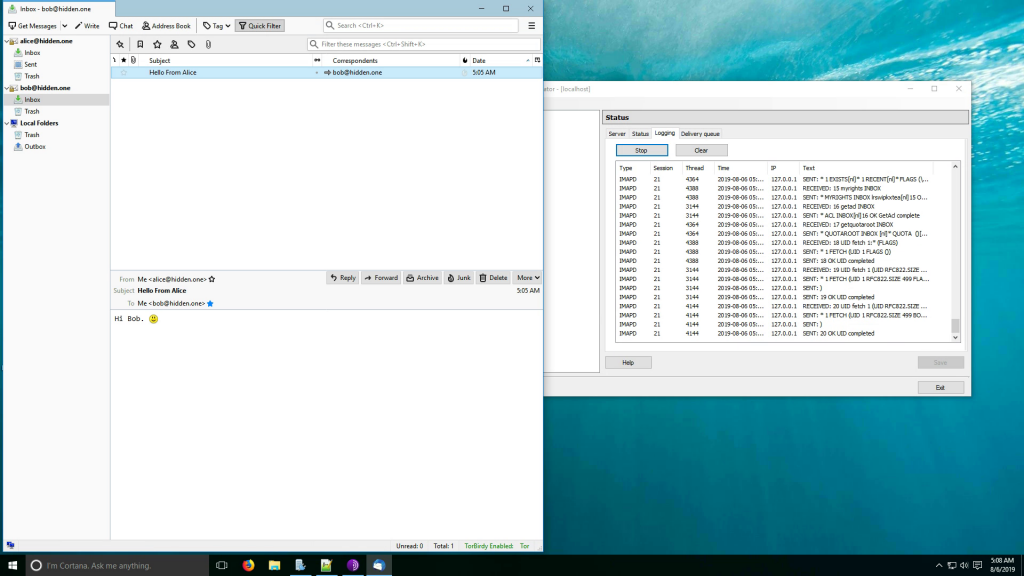
Creating Hidden Mail Service
Previously, I’ve described how to run hidden mail service over TOR and how to connect to it using ThunderBird.
In this post, I’ve create a video demo of what I’ve told in the posts.
OnionFarm WriteUp
OnionFarm was one of the challenges in UUTCTF which was held in 25-28 April 2019 by Urmia University of Technology. The challenge has been solved by 4 teams. Following, the challenge details and the write up is discussed.
VPN or TOR? This is the Problem
I just saw a post in TOR stack exchange titled “Is it recommended that we use a VPN along with Tor?” and wanted to post about using VPN and TOR alongside. Previously, I’ve posted Socks Rocks! The Good, The Bad and The Ugly and Socks Rocks Again! and this post is conclusion of the posts.
Scooby Tor! Where Are You?
I notified that the exit node IP address in the TOR browser is not the real exit node IP. Then I started to drive the mystery machine for investigating the case. Real IP! Where are you?
Connecting to Hidden Mail Server using Android
My Contribution in K9 Android Mail Client
K-9 is an attractive, open-source email client for Android with support of IMAP, POP3, SMTP, and exchange protocols. Hence, this client does not support proxy feature. This problem is referenced in #704 #980 #2619. In this post I will talk about my contribution in K-9 project by adding SOCKs proxy feature, which can be used for connecting hidden mail services.
In previous post, I described about connecting Thunderbird, an open source email client for PC, to a hidden mail service. In this post I will talk about modifying K-9 mail and connecting Android client to the hidden mail service.