I’ve playing with Android CTF questions recently and found this jewelry box. One of the questions was about a numeric one way hash question named NUMDROID. The question was presented in ASIS2014 and here, I write the write-up!
Find the Numdroid Question
The question was a file of binary data. The first bytes (known as File Signatures) show that the file is a 7ziped file. Therefore I decompressed it and found the files inside compressed file.
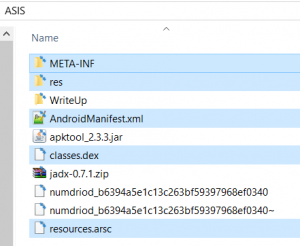
The contents extracted from the file were parts of an APK.
So I zipped the files and signed by a self signed key. For more information about signing APK archives please refer to my previous post about smali code injection.

Install is the Magic
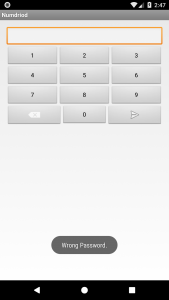
First of all, I installed the APK in order to find what does it do. It was a screen with numpad inside and a back-OK keys.
Source Code is Another Magic
For the sake of the byte code, Java code is vulnerable against decompilation techniques if no obfuscation method is used. The code was clear! I used JADX which is very good decompiler for APK files.

After a fast overview of the source code, I found that the numeric input is hashed by an algorithm inside the code and checked against a string for being verified. I highlighted the code section for hash function.

As it is visible in the isOK function, the password’s length is 7 at maximum.
Capturing the Flag
I’ve checked the next activity which will be shown after verification process. The activity shows MD5 of input number as the flag. Therefore finding the flag is about to cracking the hash function.
There are two ways for cracking:
- Crypt Analysis and finding a way to revert the hashed string to its original value, which is not suitable for this kind of challenge.
- Bruteforcing all ranges from 0 to 9999999 and calculating the hash.
I’ve select the second choice and bruteforce the range. For this aim, I’ve write a small piece of java code:

And converted it to dex file in order to access its smali code.The needed tools are javac, dx and backsmali.
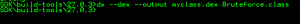
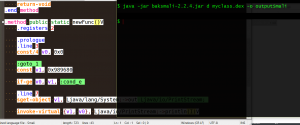
Then I’ve injected the smali code inside the APK and put my bruteforce code inside onCreate() of the main activity. The bruteforce code will write the flag in Log of Android if the hash value is correct.

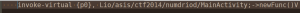

The Flag
Finally, after injection, I signed and installed the new APK on the Android Emulator and voila! the result.

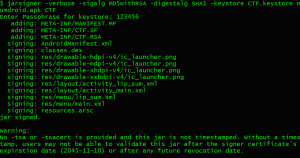


The code is MD5(3130110) and thus the flag is ASIS_{3C56E1ED0597056FEF0006C6D1C52463}.



