Ilam CTF has been hold on 23rd Nov 2018. Unfortunately I’ve planned other things for 22-23 Nov 2018 and because of the delay in holding the CTF, I couldn’t attend this CTF.
However, I could download the Android Reverse question for future analysis. And the flag is here:
ilam_ctf_0a095194dbcf4f798751aaafdfb_1db6b2ed339f4698b6b38b5e7ae
But the WriteUP!
Start to Android Reverse WriteUp
I’ve installed it on an emulator and the application crashed.

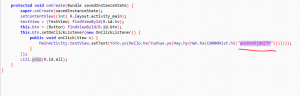
I’ve analyzed the crash logs and found an arithmetic exception at MainActivity:

Using APK Studio and JADx I’ve found and fixed the division be zero which was put in the code.

After that I’ve found that the key was hidden in some functions, in which they are playing with an initial String (aWxhbV9jdGZfM).
Analysis
Then I just copied the code of functions to my Java editor and started to play with them.
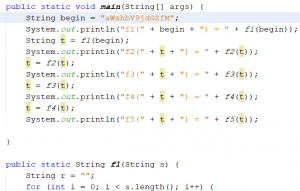
The result was something like this:

As you see, the results from f3 start to change in characters. I mean, they all looks like base64 till f3 but then, they change to something odd.
I’ve checked the functions. All the functions change a part of input string and add a new part to it. I though that it was an encrypted string but I did not found any cryptographic function call or even dynamic call inside the code. Then the Key should be Base64 Encoded!
The Flag
As a simple test, I just put the parts together and decoded them.
Voila. The flag was in there:

There was just a point. They have added an extra part to the base64 encoded text which I removed it. You can find the extra part at Yoyo.yo function which ends with an arithmetic exception.
Therefore, the flag is:
ilam_ctf_0a095194dbcf4f798751aaafdfb_1db6b2ed339f4698b6b38b5e7ae
The original APK is attached here for who may interest.