I notified that the exit node IP address in the TOR browser is not the real exit node IP. Then I started to drive the mystery machine for investigating the case. Real IP! Where are you?
Motivation for Scooby Tor!
Someone in Twitter asked me an interesting question which I wasn’t noticed before. The question was:
Why the IP address which is shown in whoer is not same as the exit node which is shown in TOR Browser?!
Shadow
Therefore I started to investigate the cause which was very interesting.
I think this problem has a similar situation of the Scooby Doo series. There is an unknown subject (the IP address displayed in whoer), the bad guy behind the ghost mask (the IP address shown in TOR Browser) and the clues!
The Question
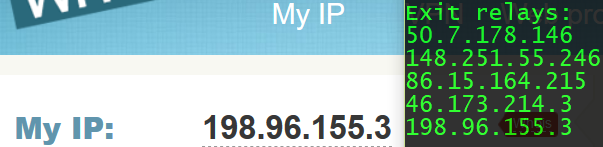
In the first step, I myself checked the case in order to see the task and verified. I tested with whoer and whatismyip. The results are the same.
The Steps
We now faced the ghost! and Scooby started to fear of the case. But with the help of Velma, they started to collect the clues.
The first think that I did, was finding the exit nodes of Tor in other way. I connected to TOR control port using telnet, but I had to define a password for connecting to it.
Adding Password to TOR Control Port
Using the following command, one can generate a hashed password for TOR:
tor --hash-password password > pass.txt
Then enter the VALUE inside pass.txt to the TOR config file, torrc which is inside the TOR Browser folder if you’re using windows or in /etc/tor if you’re using *nix systems, as the following:
HashedControlPassword VALUE
The VALUE is something like 16:HASHEDVALUE. Now you can restart TOR and connect to TOR control port or use the charming python script in order to display the list of exit nodes. Credits go to TOR stack exchange. But I’ve changed some parameters:
- First of all changed the control port from 9051 to 9151 which is the default port for TOR control port.
- Then added my password to the
authenticate()functions. - Run the script
All the things are OK. The ghost IP address is changed but you can see the list of exit nodes. Here is the proof:
Therefore, TOR creates multi circuits and use them as the connection manager. But the circuit which is used for displaying the exit node to the user may not be the same as real exit IP address.