Onion Harvester

The TOR network is a service for browsing and surfing the Internet anonymously. It hides the address of the client through 3 layers of encryption which the encryption starts at the client itself. The picture below, shows the process:
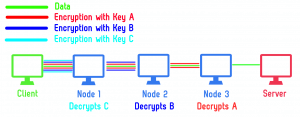
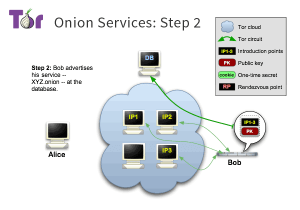
It also allows the services to be served hidden, which means no one knows the IP address of the service. These services are called hidden service. The hidden services should be accessible through a system like DNS in the Internet. But DNS leads to legal information and IP disclosure which is not acceptable by TOR. Thus, TOR has its own DNS system named Hidden Service Directory (HSD). The HSD is a Distributed Hash Table that contains the Onion Services introduction points. For more information check the TOR project’s description page in this link.
Therefore I’ve started Onion Harvester project for having an updated list of alive Onion Addresses in the TOR Dark Web. Firstly I’ve developed a simple Java application that brute force all the addresses of TOR with default web ports (80 for HTTP and 443 for HTTPs). Then with the help of my friend, I’ve changed the standalone brute-forcer to a fully distributed brute-forcer in which volunteers can join the project and search for Onion addresses.
All they should do is to have Java 8 and TOR installed on their system, and run the Onion Harvester Client. Because the Java and TOR is multi-platform, the client does not have any dependency and can be run on all platforms and OS (Linux, Windows, MacOS – x86, x64).
Contact me if you want any question
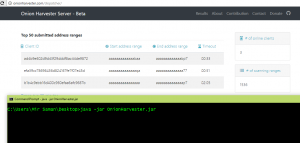
ScreenShots

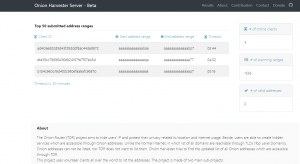
Contribution
The more volunteer clients join, the more updated list will get. If you want to help for finding the addresses, you can download and run the Onion Harvester Client. In current phase I need contribution in these areas:
- Developing the client on other languages (C#, Python, Perl, Ruby, C++, …)
- Running clients to speed up the searching
