Barnamak WriteUp
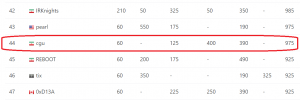
Two weeks ago, SharifCTF was hold and the questions were acceptable. We attended with CGU team name and and gain the 44th place among the 682 attended teams, whom has at least one question solved in the CTF. In this post I described the writeup for the question about reverse engineering of Android app with 200 points (the 3rd question of reverse section).
The App
The app for the question is available for downloading, however, you may download this link if you like. By the way, the task name was barnamak.
In the first step, I installed it on an emulator to watch what it wants.
adb install Find_Flag.apk

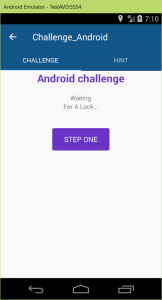
Step One
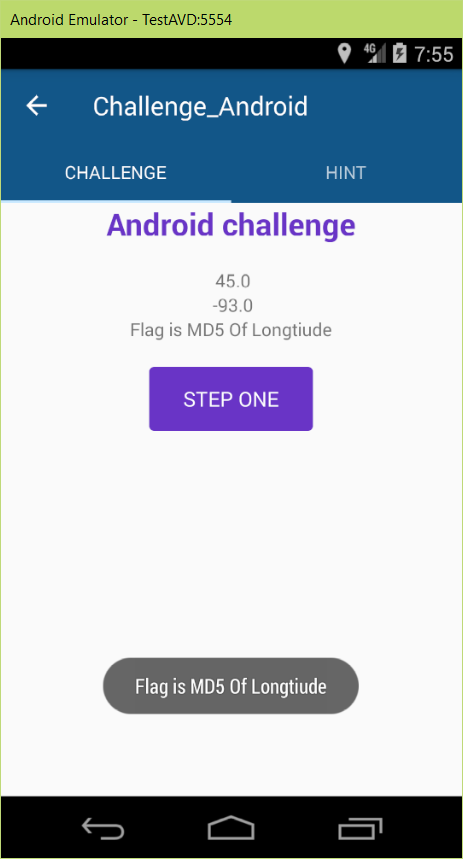
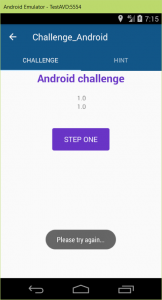
It said that “Waiting For A Lock…” and the location icon started to blink. So probably it waits for location. I gave it a try by setting a location.
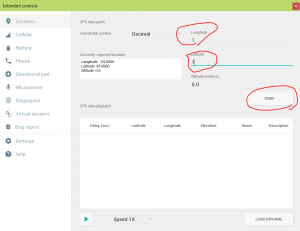
It is OK. The app got the location.

I’ve pressed STEP ONE and got the message: “Please try again …”
So it is worth it to investigate around it. After that I decided to check the source code for the app. The famous DEX2JAR and JD-GUI helped me alot.
I’ve convert the APK to JAR file using dex2jar:

And opened with JD-GUI:

I’ve found that the piece of code when the button pressed is located in b() in com.challenge_android.fragments.ChallengeFragment.class where the code is:

It says j = 0x2C = 44 and i = -0x5B = -91. Then it checks the input location:
if (((int)this.location.getLatitude() == j + 1) && ((int)this.location.getLongitude() == i - 2))
Therefore, the latitude of location should be j+1 = 45 and longtitude should be i-2 = -91-2 = -93
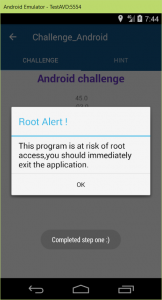
Posting these values made a change in app. I did another thing. The app checks rootability of phone using com.challenge_android.a.c class and some things happen inside it. So I’ve changed my phone to be root. The com.challenge_android.a.c.c checks the existence of a folder named /dev/com.koushikdutta.superuser.daemon/ and I created the folder and got ROOT :).

Step Two
After that app suddenly closed. The final thing was omitting the application termination.

The noisy code was at com.challenge_android.fragments.ChallengeFragment.a() that can be bypassed by smali code injection and removing the part of code. For more information about smali code injection, you may follow my post about the subject.
Voila! The flag appeared.
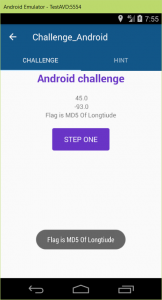
Flag is MD5 Of Longtitude: SharifCTF{MD5(-93)} = SharifCTF{87a20a335768a82441478f655afd95fe}